
Connecting to 20.000+ smart homes with Loxone Miniserver, Gira X1, HomeServer and a variety of KNX IP Interfaces gave us a unique opportunity to do some thorough research together with our users. We have researched how they use smart home mobile apps remotely, how system integrators remotely program their customers’ homes and how smart home owners use our voice control services.
If you are using your smart home mobile app on the go, if your system integrator programs your home remotely or if you are using our Cloud voice control product, then it’s likely that you have a port forwarding set up.
What is Port Forwarding?
Port forwarding is a networking technique through which a gateway or similar device transmits all incoming communication from a specific port to the specified port on any internal network node. Port forwarding enables an external source network or system to connect to an internal source port, which typically connects to Internet services and an internal private LAN. Port forwarding is also known as port mapping, tunneling or punch through.
What is the exposure?
There are complex techniques available that enable scanning all ports on a dedicated IP address - with this it can be figured out where specific service is located. Over the network your ports can be marked and their status checked - theoretically enabling intruders to try and establish a connection with your smart home gateway.
However, with the Gira X1, Gira Homeserver and Loxone Miniserver, there is still authentication in the form of a username and password that are required to connect to home’s gateway. From a security standpoint - that makes it as hard to penetrate as your email or social media account.
On the other hand, most of the users with KNX IP Interface - a lot of them access network from outside in the same way - that use Port forwarding have a big security exposure. Since there is no additional authentication in place on the gateway, once the open port is scanned, the connection to the gateway can be established immediately.
What is the exposure if an intruder establishes a connection to a smart home?
Well, it depends on the type of your smart home gateway. But in all cases it means a lot of effort with not much gain for the intruder so these events are highly unlikely to happen.
In general, if no critical devices are exposed (we highly recommend not having locks, alarms, door or window openers, etc. connected to the smart home gateway), the worst thing that could happen is the intruder turning lights on and off or rolling your blinds up and down.
With the Gira X1 and Gira Homeserver (if KNX IP ports are not forwarded) this is your biggest exposure.
With the Loxone Miniserver - once the connection is established with the right username and password- your Loxone config can also be accessed . Loxone config enables access to reconfiguring your smart home - in theory this means your configuration could be damaged and smart homes functions broken. It is very important that the Loxone mobile app username and password are different to the Loxone admin username and password.
The exposure of KNX IP Interface users is the most relevant. Once the intruder establishes a connection - not only that the devices can be controlled but with some further effort the smart home could be reconfigured not to work.
How can I avoid Port Forwarding?
In most cases there are solutions that enable avoiding port forwarding but they are dependent on what you want to achieve. Whether it is establishing a secure remote connection with a mobile app, use our voice control services or program smart homes of customers remotely in a secure way.
Avoiding Port Forwarding with voice control
You can avoid port forwarding when using our voice control product either by acquiring or building (DIY) our 1Home Box. 1Home Box establishes a dedicated encrypted connection between a smart home and the 1Home Cloud system. It is accessible only by devices with an installed unique 1Home certificate.
Avoiding Port Forwarding with remote control & programming
VPN
The most common technique used to avoid Port Forwarding for the purpose of secure remote control & programming.
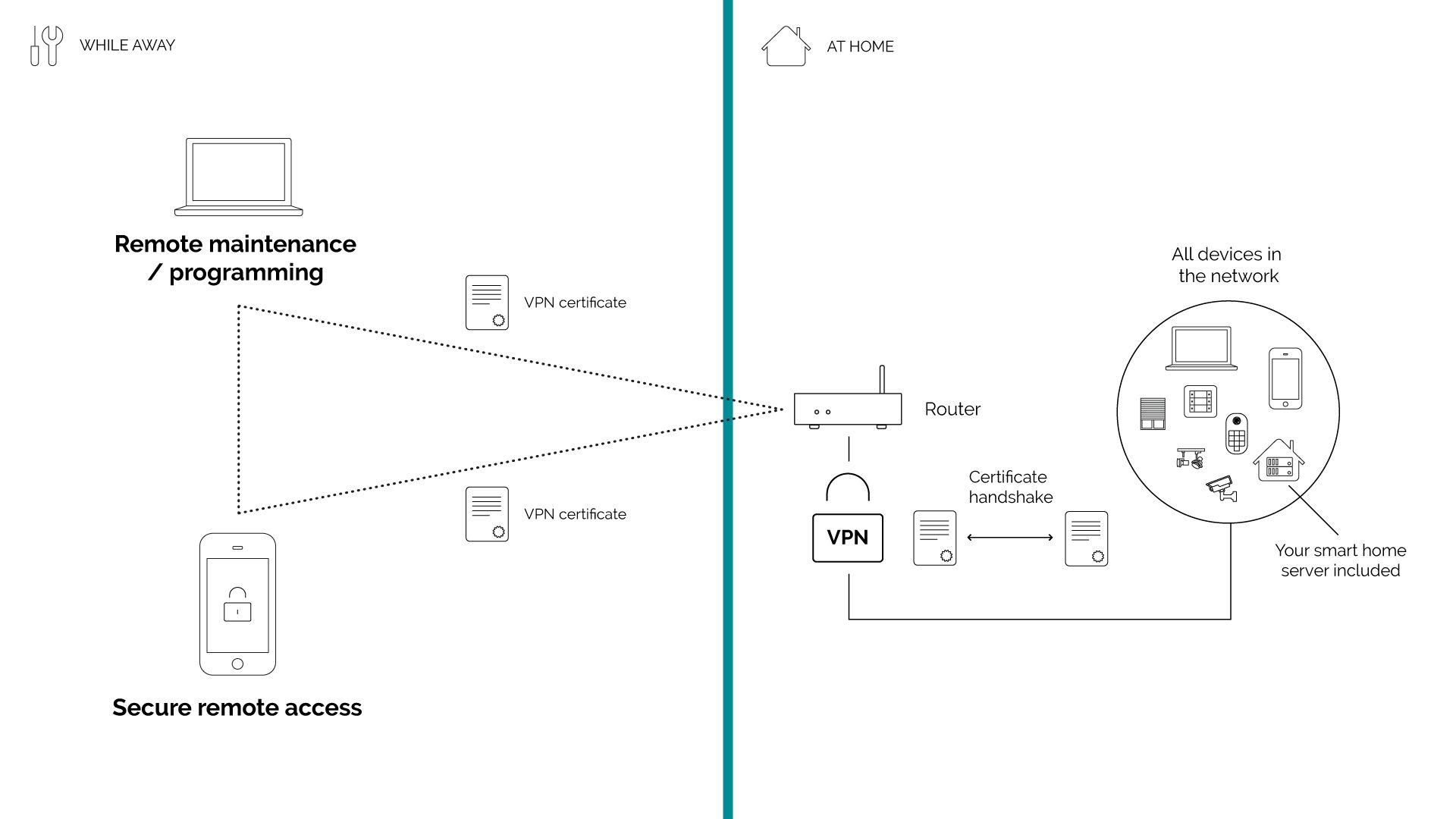
What is a VPN and how it works?
The most common implementation of a VPN solution uses password-protected certificates issued by trusted Certificate Authorities. A customer first needs to get/create a certificate, which is then installed on their local computer or mobile phone. When the connection is being established with the configured VPN Server, the certificate needs to be presented in the “handshake” process. Based on defined VPN Server configuration, a customer with the presented certificate gets access to the appropriate part of the underlying network.
How do you use a VPN?
As a smart home owner you will get a mobile app installed on your phone (like theOpenVPN app). When you want to use the secure connection, you open up the app and turn the VPN on. After that, you continue controlling the home through your smart home mobile app, as usual.
The same process awaits a system integrator that wants to securely program the home remotely. The only difference is, that in most cases, as a system integrator, you will be using the app on your computer. Simply open up the app, turn the VPN on and continue programming the home via dedicated software (Loxone Config, KNX ETS, Gira Experte or Gira Project Assistant).
1Home secure remote control & programming
In comparison to a VPN which normally establishes a connection to your router and with that enables access to all devices in the network - 1Home solution is dedicated to your and only your smart home devices.
A lot of system integrators are reporting a VPN connection is too much of a responsibility for them as they neither want nor need access to a complete network. At the same time a lot of users share the same feeling and do not want to expose their entire network to the system integrator.
We are tackling that with a solution that is based on security keys and is running on the 1Home Box device.
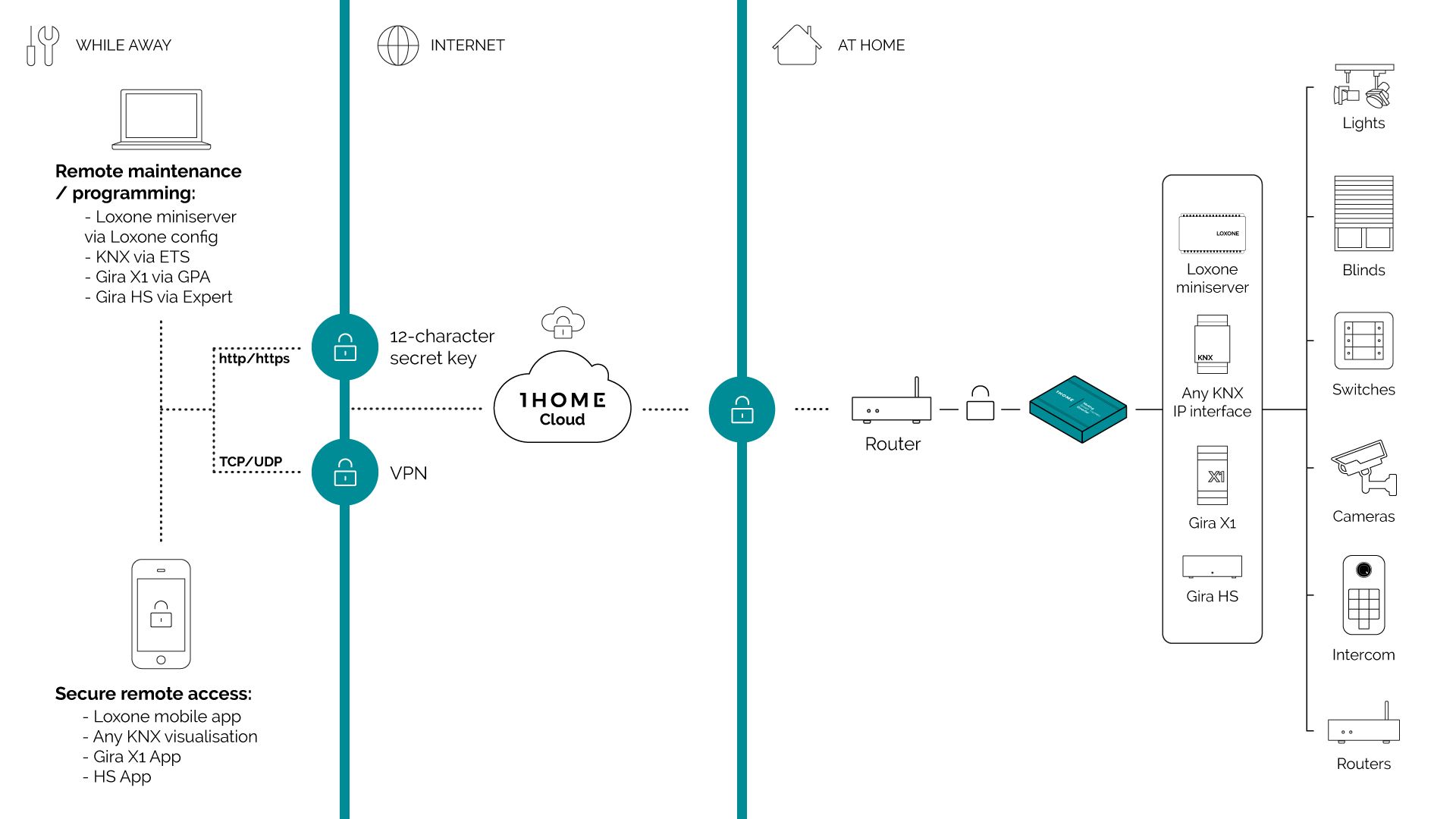
1Home Box device opens an encrypted connection between a customer’s smart home server and 1Home Cloud system. We then have two solutions for securing a connection between client application or installer’s programming tool and the cloud system. In case of HTTPS (and HTTP - if client application supports both HTTP and HTTPS) protocol, the communication can be protected with 12 character secure key. In case of UDP and TCP we have implemented a modified VPN type of a solution.
Next to establishing a secure connection to a smart home gateway - customers can also create custom remote connections to other devices in their smart home that support HTTP, HTTPS, TCP or UDP connection. This way they can also safely access installed security cameras, intercoms, network routers and many other smart home devices which can then be accessed remotely in a secure way.
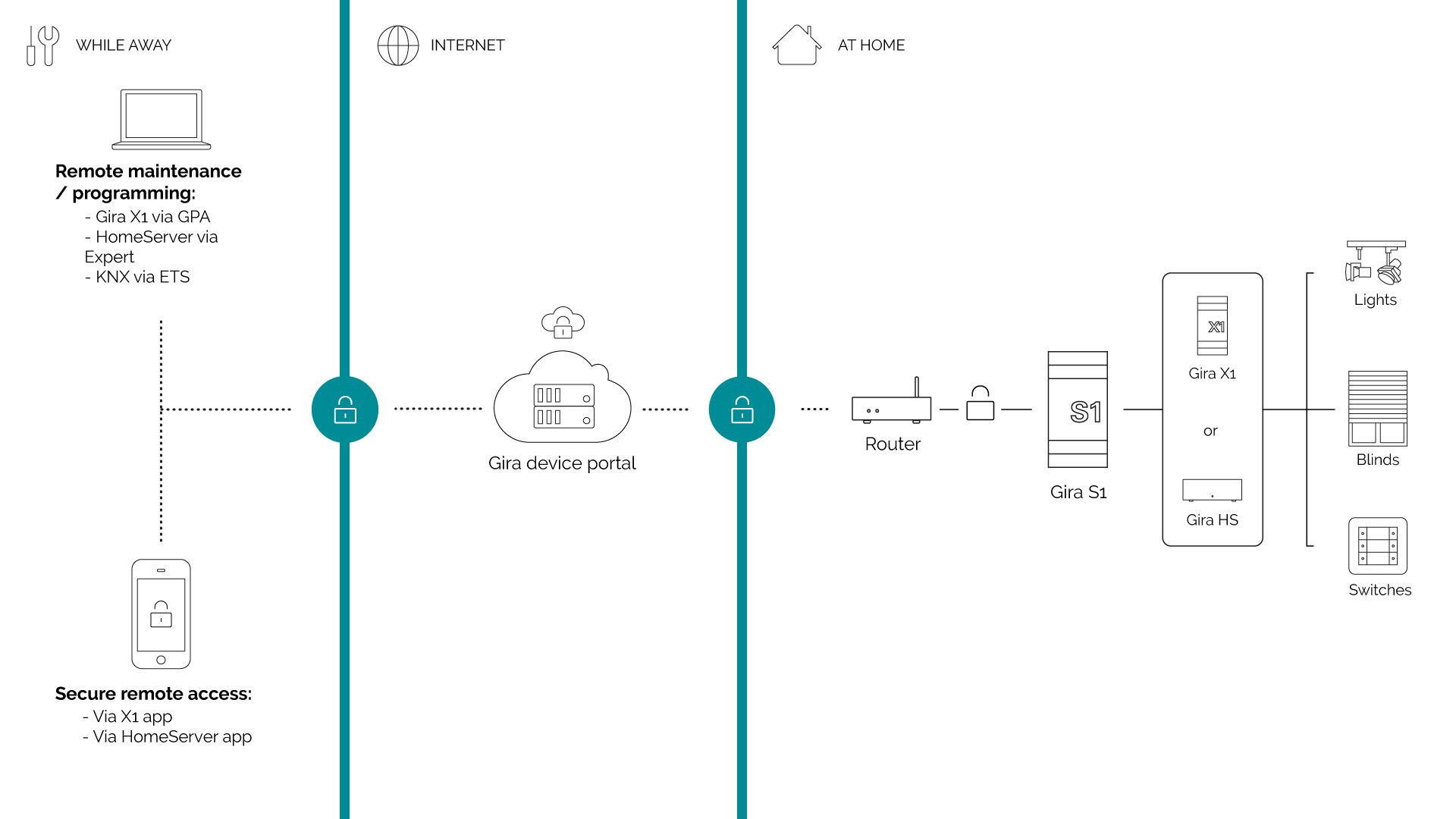
Gira S1 (doesn’t work with Loxone Miniserver)
Gira S1 was one of the first solutions on the market tackling this problem. It works in a very similar way as our Remote access & management product but is locked inside the Gira ecosystem and only works with Gira X1 and Gira Homeserver. It also works with KNX IP interfaces but only for programming the home (via KNX ETS). At the same time, S1 will only enable you to securely use your mobile application with your smart home gateway. Other devices like cameras, intercoms and network routers - can only be accessed remotely through the web based Secure Device Access portal (https://securedeviceaccess.net/).
The S1 will enable a smart home owner to remotely control their home in a secure way and at the same time - enable a system integrator to securely program without an on-site visit.
Things to consider before setting up port forwarding:
To conclude, here are the main points to help you be secure and at the same time avoid overengineering your smart home.
- Assess your exposure. When thinking about security - a very big question to ask yourself is: why would someone be motivated to connect to my home? This question gets treated very differently whether you are an engineer or a high-profile military employee.
- Do not expose critical devices. Locks, alarms, doors, windows, gates, garage doors (etc.) shouldn’t be connected to your smart home server when doing port-forwarding.
- Do not leave ports open on the KNX IP Interface. As mentioned above, the lack of authentication on the gateway is a big security exposure. We don’t recommend port forwarding on the KNX IP Interface. If you are comfortable in knowing what you are doing and still want to move forward - set it up for a quick test and then close it down. Also make sure that if you are using Gira X1 or Gira Homeserver, you don’t have any ports open on the accompanying IP interfaces in those servers (IP interfaces are a building block of the Gira X1 and Gira Homeserver).
- If using Loxone Miniserver, Gira X1 or Homeserver - make your password strong and don’t leave it on default value. The password should be long (12+ characters) and include lower and upper case letters, numbers and special characters. If you are using a Loxone Miniserver - make sure your Miniserver password doesn’t match your Loxone Config password.
Do you have any concerns about your particular smart home configuration or feedback about this?
Let us know, we will be happy to help and discuss how this important subject can be dealt with in the best way possible to offer a peace of mind in a world that is becoming more connected by the minute.
